How to create a ChildWindow Login Popup for Windows Phone 7
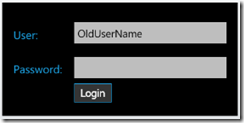
Introduction After struggling with a navigation issue in my app of when to show/go to/return from the Settings page that captured the user name and password, I decided to pop up a window on any page where and when credentials were necessary but not currently known. Since I knew I was going to add more credential-requiring pages in my app, using a popup allowed me to reduce my dependency on navigation silliness between the pages, and have a more encapsulated design. This post will show you how to pop up a ChildWindow on the app page to grab the user’s login credentials. The control allows the old username and password to be passed into the control so that previous values can appear. The tab order/enter key switches from textbox to textbox to button. The sample application included in this post just displays the results on the calling page. Acknowledgements Several other posts helped me along the way: Jesse Liberty’s video “C...